Raising the Bar: Quality Gates for AI-Generated Code
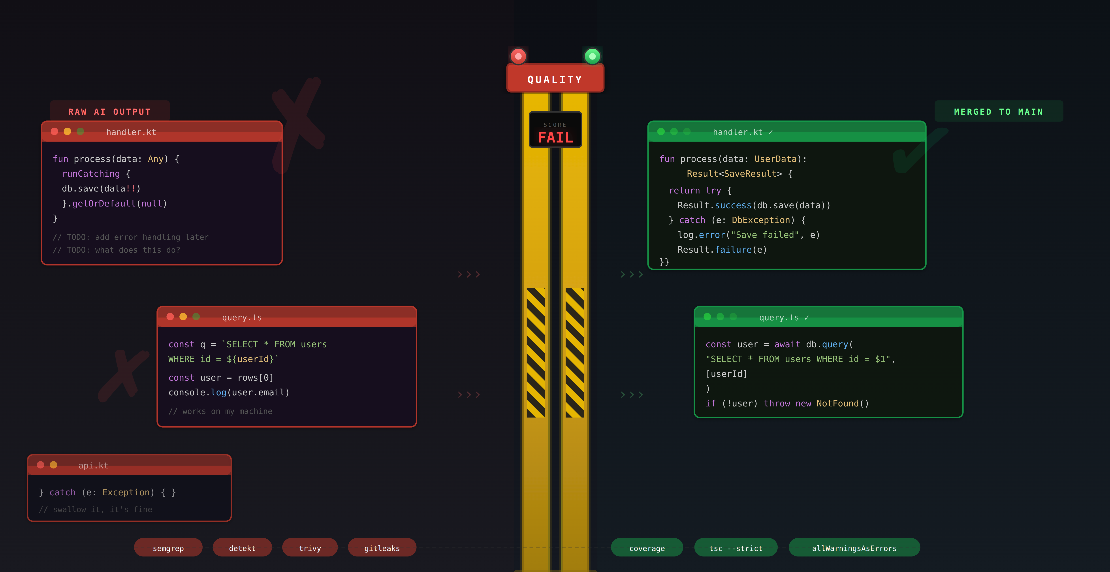
AI coding tools let your team ship faster than ever. That is the pitch, and it is not wrong. But nobody talks about what you are shipping. Right now, most teams use these tools to produce broken software at unprecedented speed.
Security holes, silent data corruption, exception handling that hides failures. None of this shows up in your sprint velocity. It shows up when the product collapses under technical debt, or when a customer hits an unhandled edge case in production. If your team uses AI coding tools without guardrails, you are not moving fast. You are accumulating landmines.
Read More
