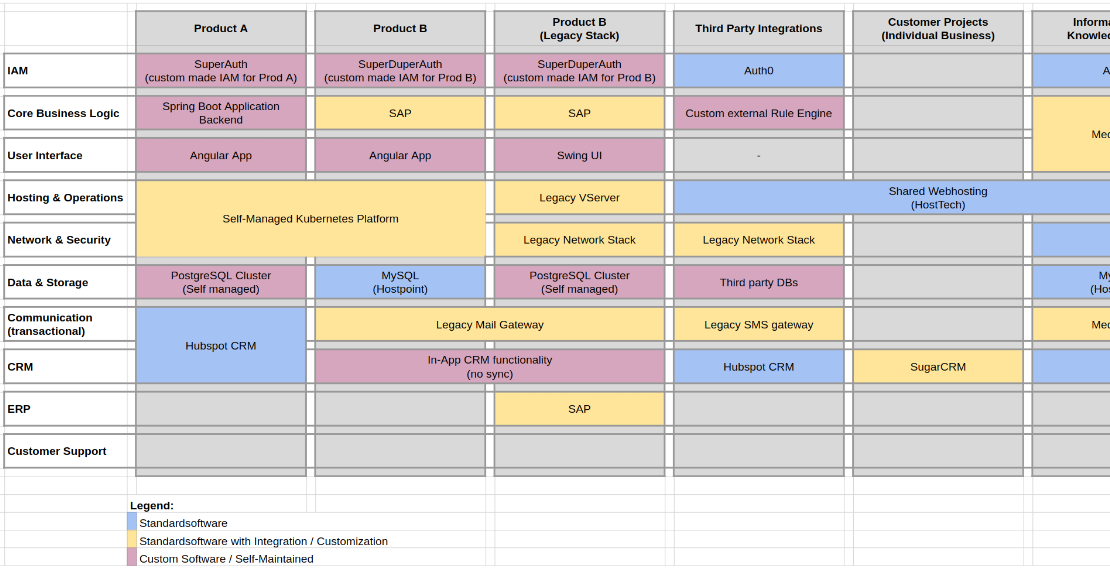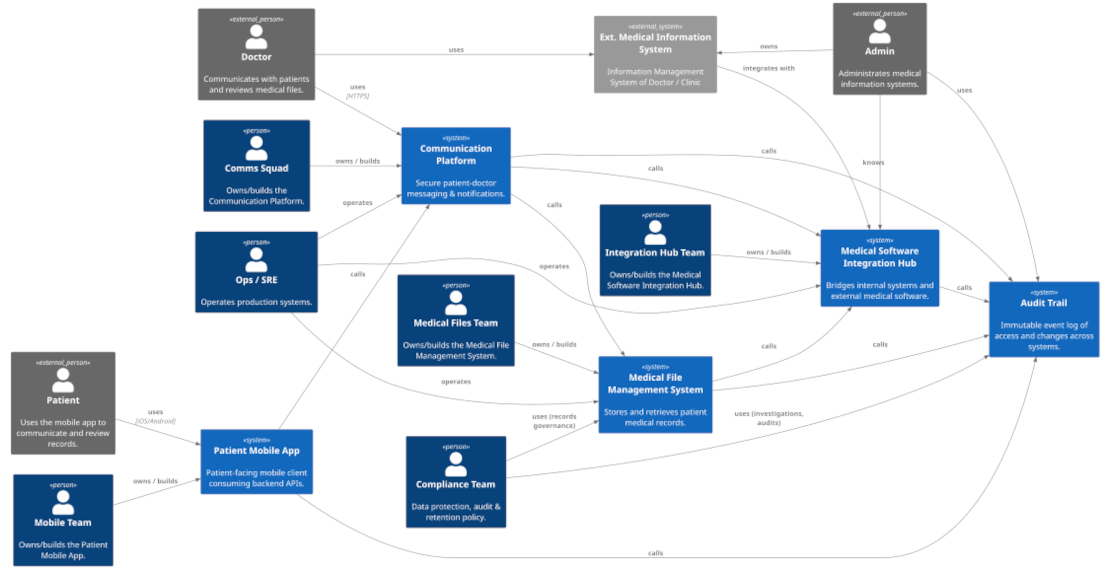
How to Map Your System Landscape in One Afternoon – The C1.5 Shortcut
You’ve just stepped into a new role – maybe as CTO, maybe as Head of Development – and as usual, the architecture is a maze or even completely missing. Documentation is outdated, knowledge is scattered, and no one holds the full picture. Without a map, you’re flying blind.
You could spend weeks reading thru confluence, readme and code, piecing things together, but there’s a shortcut:
In this post, I’ll show you how to map a “good-enough” system landscape in one afternoon using a lightweight, practical shortcut of the C4 framework I call C1.5.
Read More